
Tips for completing a risk assessment, mitigating risk, and making informed choices when deciding on a cybersecurity strategy for your organization.

Data breach prevention tips from a panel of cyber security experts. Recorded panel discussion.

2015 Cloud Security report put together by Alert Logic.

What you need to know as a company looking to hire talented security personnel in a “cybersecurity labor epidemic”.

To help with implementing DevSecOps into your organization, here is a summary of 10 Practical Security Tips for DevOps as put together by Alert Logic.
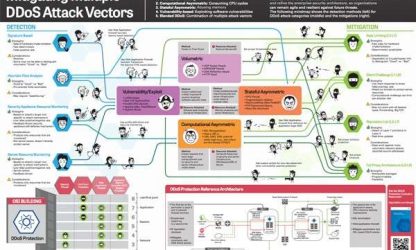
Infographic from F5 with detection and mitigation tactics for multi-vector DDoS attacks.

Recap of WTIA IT security panel discussion concerning data breaches and cybercrime prevention
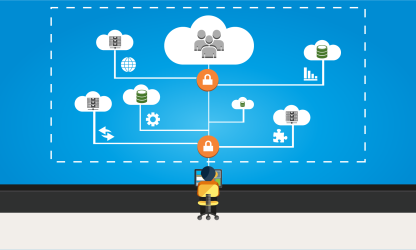
Webinar discussing tactics for setting up a secure, maintainable, hybrid cloud deployment

Venom, announced recently by CrowdStrike is a vulnerability affecting the floppy drive emulation code used by many virtualization platforms.
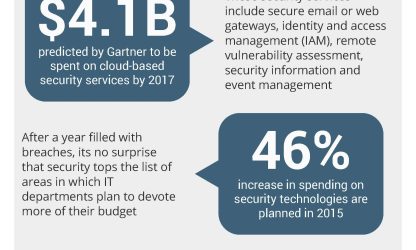
Security-as-a-Service infographic shows cyber threat landscape, security trends, what security as a Service is, and what to look for in a security provider

Cloud vs Colo event recap, Security-as-a-Service infographic, A rundown of shutdowns for businesses in 2014, Singapore as the gateway to China

Cybercrime is on the rise. Companies, large and small, are falling victim to a fully weaponized web that make cybercrime easy to perform.