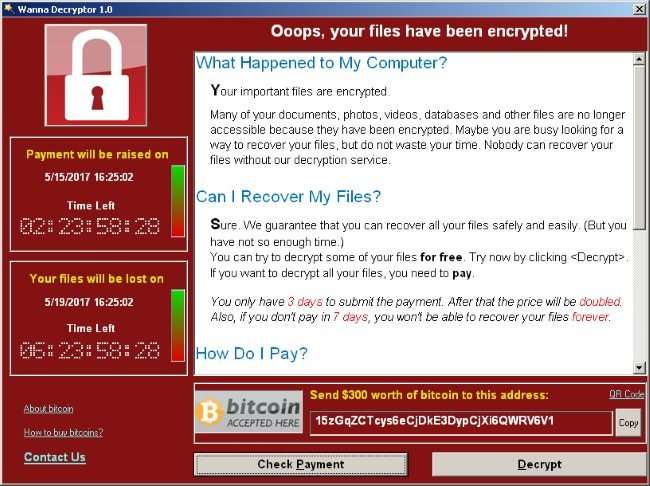
WannaCry is the most severe malware attack this year, and the spread of this troubling ransomware is far from over.
Researchers estimate that nearly 57,000 computers in more than 150 countries were infected by the end of the day Friday. While the spread slowed down a bit on Saturday, it had hardly stopped. As of Monday morning, more than 200,000 systems around the world are believed to have been infected.
What is WannaCry and what does it do to your computer?
WannaCry searches for and encrypts 176 different file types and appends .WCRY to the end of the file name. This malware is a type of trojan virus called “ransomware.” As the name suggests, the virus in effect holds the infected computer hostage and demands that the victim pay a ransom to regain access to the files on his or her computer. It works by encrypting most or even all of the files on a user’s computer. The software then demands a ransom be paid in order to have the files decrypted.
In the case of WannaCry specifically, the software demands that the victim pays a ransom of $300 in bitcoins at the time of infection. If the user doesn’t pay the ransom within three days, the amount doubles to $600. After seven days without payment, WannaCry will delete all the encrypted files and all data will be lost.
Can you recover the encrypted files?
Decryption of encrypted files is not possible at present. If you have backup copies of affected files, you may be able to restore them.
In some cases, files may be recovered without backups. Files saved on the Desktop, My Documents, or on a removable drive are encrypted and their original copies are wiped. These are not recoverable. Files stored elsewhere on a computer are encrypted and their original copies are simply deleted. This means they could be recovered using an undelete tool.
Who is impacted?
Any unpatched Windows computer is potentially susceptible to WannaCry. Organizations are particularly at risk because of its ability to spread across networks and a number of organizations globally have been affected, the majority of which are in Europe. However, individuals can also be affected.
Best practices for protecting against ransomware?
- New ransomware variants appear on a regular basis. Always keep your security software up to date to protect yourself against them.
- Keep your operating system and other software updated. Software updates will frequently include patches for newly discovered security vulnerabilities that could be exploited by ransomware attackers.
- Email is one of the main infection methods. Be wary of unexpected emails especially if they contain links and/or attachments.
- Be extremely wary of any Microsoft Office email attachment that advises you to enable macros to view its content. Unless you are absolutely sure that this is a genuine email from a trusted source, do not enable macros and instead immediately delete the email.
- Backing up important data is the single most effective way of combating ransomware infection. Attackers have leverage over their victims by encrypting valuable files and leaving them inaccessible. If the victim has backup copies, they can restore their files once the infection has been cleaned up. Organizations should ensure that backups are appropriately protected or stored off-line so that attackers can’t delete them.
- Using cloud services could help mitigate ransomware infection, since many retain previous versions of files, allowing you to roll back to the unencrypted form.
For more on WannaCry ramsomware, here is a comprehensive blog post that provides more useful information.
For insights into where your company might have security vulnerabilities, schedule a risk assessment with one of our security experts here.