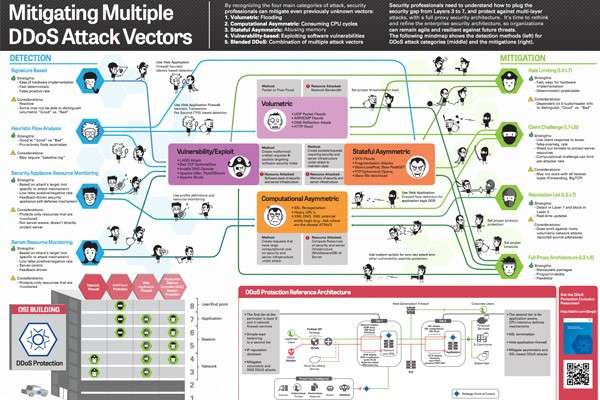
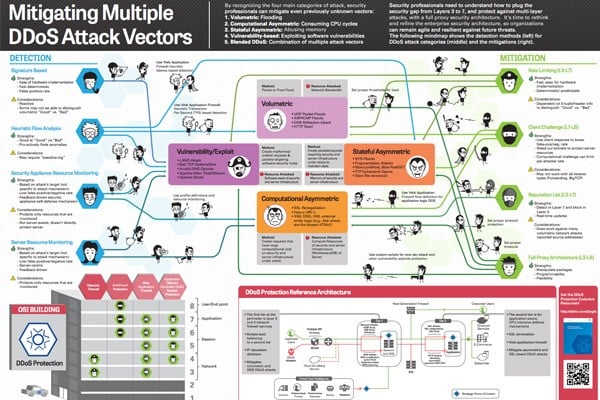
Over 80% of cyberattacks use a multi-vector approach to disable a network or servers. This approach is very popular with attackers because it has the potential to create the most primary and collateral damage to a business. The odds of success are much higher due to the complexity of the attack – they target several different network resources, or use one attack vector as a decoy while another, more powerful vector is used as the main weapon. Organizations need to be prepared to deal with these large scale multi-layer cyberattacks in a way that results in little to no effect on their business, brand, day-to-day operations or clients.
Here are the main cyberattack types that IT leaders and security experts need to be aware of, and be able to detect and mitigate:
- Volumetric: Flooding
- Computational Asymmetric: Consuming CPU cycles
- Stateful Asymmetric: Abusing memory
- Vulnerability-based: exploiting software vulnerabilities
- Blended DDOS: Combination of multiple attack vectors
Below is a great “mindmap” infographic put together by F5 that shows detection methods and mitigation tactics for the DDoS attack categories listed above. Read on!
(Click on the link below for the full infographic.)
Mitigating Multiple DDoS Attack Vectors – infograpgic put together by F5