Rock-Solid Cyber Security
Risk Assessment
Risk Assessments
Overview
World Class Cyber Security Risk Assessment to Protect your Organization
Tech leaders are talking about cybersecurity in their boardroom meetings. However, 66% of those leaders are not fully confident their companies are properly secured against cyberattacks – How secure is your organization?
As your company grows and increases its technology needs, vulnerabilities and entry points will also become more critical to your business systems. To deal with these never-ending threats, you must design and implement advanced security testing policies before a crisis occurs. Waiting until an attack has started can mean the difference between a small issue and a true crisis.
Definition
Learn more about Security Risk Assessments
What is a Security Risk Assessment & why is it important?
An Information Security Risk Assessment is the entire process that goes from Researching, Identifying, and Evaluation potential risks at organizations to Designing and Implementing data protection plans. We can say that the goal of a security assessment is to help protect both people and property that might be at risk to a variety of crimes.
Due to advancement in technology and the rapid growth of companies worldwide, organizations are more exposed to information security risks that might potentially have an adverse impact to their goals and objectives. Then a Cybersecurity risk assessment becomes an integral part of an organization’s enterprise risk management process.
An Authentic Security Risk Assessment will help your organization by:
- Understanding the organization and identifying the people and assets at risk.
- Determining scope of systems and assets supporting key lines of business or processes
- Identifying related systems, assets (Networks, servers, applications, data centers, tools, etc.), regulatory requirements and/or compliance mandates.
- Creating risk profiles for each asset and understanding what data is stored, transmitted, and generated by these assets
- Identifying threats, vulnerabilities, impact, and likelihood of harm that will occur. This includes the overall impact to revenue, reputation, and the chances of a firm’s exploitation.
- Benchmarking business practices
- Prioritizing remediation steps in an effective plan based on your company’s specific goals, budgets, and timelines.
Common Problems Observed in poor Security Risk Assessments:
- Poor articulation of risk scenarios – Usually executives get Risk Scenarios describing vague and generic events without articulating specific threats, vulnerabilities, assets, and consequences.
- Identification of risks using a compliance-oriented approach – A compliance-oriented approach towards risk assessment drives a “checklist” behavior, giving a false sense of security that an organization is not exposed to any risks if they fulfil all compliance requirements.
- Absence of risk tolerance – Cybersecurity risk tolerance at the enterprise level is often ignored, and management face difficulty in deciding the appropriate level of risk-taking to adopt whilst in pursuit of their organization’s business objectives.
- Treating risks with irrelevant controls/measures – Organizations may get a broad approach in producing measures to mitigate identified cybersecurity risks, resulting in the implementation of controls that don’t address the root cause.
StrataCore’s Approach
StrataCore’s Approach
StrataCore’s cybersecurity sourcing methodologies and tools are adapted to suit your environment and business objectives.
An Information Security Risk Assessment will help you align your cybersecurity activities with your business requirements, risk tolerances and resources.
Our consultative approach provides a mechanism that enables you to view and understand the characteristics of your strategy to manage security risks.
Our cybersecurity consulting partners employ tested techniques and best practices to effectively identify, analyze and monitor information related vulnerabilities, spot potential data privacy and security compliance issues, and help you prioritize remediation steps in an effective plan based on your company’s specific goals, budgets, and timelines.
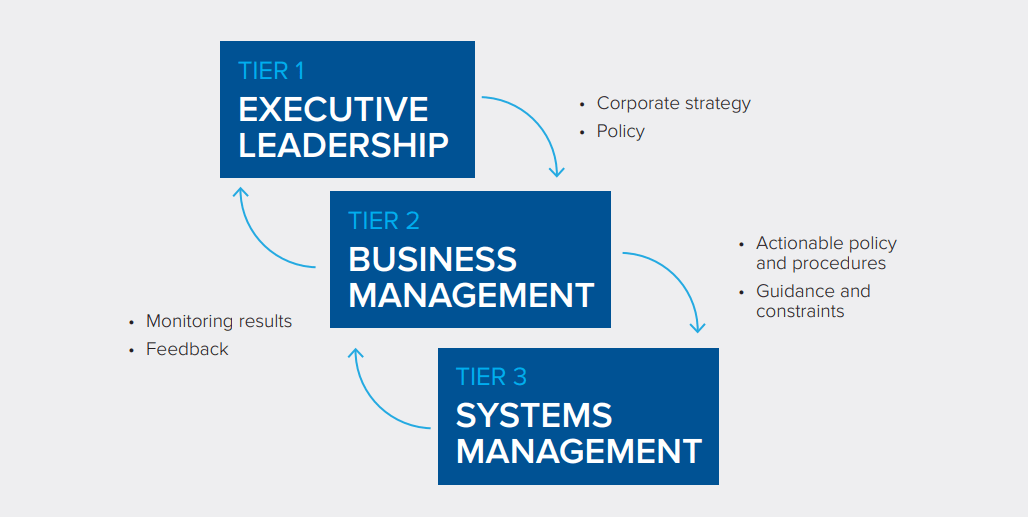
The StrataCore Difference:
Knowledge of your technology tools
The StrataCore team has many years of IT sourcing experience, giving us a deep understanding of technology tools and service providers.
A better framework for governance
We ensure risk assessments meet the unique needs of each client’s business goals and industry challenges.
By providing sourcing expertise on everything from risk advisory and compliance assessment to technical testing and monitoring, we can help your company create a data security risk strategy that strengthens your ability to absorb and react to emerging threats while meeting regulatory compliance mandates.
A non-biased approach
We have a vendor-neutral approach to help you source the right IT solution.
This allows us to stay objective when we provide comprehensive, integrated and business centric recommendations that help improve the effectiveness, efficiency and agility of your cyber risk management and compliance strategies.
Related Resources

8 Critical Redlines for IT Services Contracts
Words matter when you’re doing business and it’s easy to get trapped in a bad contract if you’re not familiar with the technology language.

Evolve Your Business with the Help of an IT Broker
IT service brokers, such as StrataCore, exist to make your life easier by becoming your dedicated expert and advocate in the technology space.

Cryptocurrency: Between Scams and Salvation.
Is Cryptocurrency good or bad? Discover here some of the most relevant examples that will help you clarify your doubts.

No Shame Security
This article is not intended to make you a security champion. However, we will arm you with the knowledge to identify some red flags.
Approach
STRATAGY
Technical expertise and vision to help you develop a plan or technology roadmap.
STRATACARE
Real support from real people to help with implementation, management, and billing.
What Our Clients Say
-

Steve Talt
Sr. Director, Systems @ Getty Images“StrataCore’s team worked on our behalf to source the best solution for our needs. They helped to save us valuable time and money.”
-

Wayson Vannatta
CIO @ WatchGuard"When it comes to getting IT services, colo or a security vendor, the first partner I call is StrataCore. I count on them to know the heartbeat of the market and the best options for our business needs.”
-

Brian Capps
Director, Network & Data Center @ Zillow“StrataCore hires good people, the team has been super solid and enjoyable to work with.”
-

Brian Hanson
Sr. Director, Comcast Technology Solutions @ Comcast“The StrataCore team has helped immensely over the years. I don't have to augment my team with experts - you fulfill that role.”
-

Jai Dalal
VP, Internal IT & Technical Client Services @ WideOrbit“The value that StrataCore adds to an IT department is huge. This is especially the case when you have a lean organization that doesn't have the bandwidth to vet the market to obtain strategic pricing or services.”
-

Nick Halden
Solution Architect @ Vix Technology“The StrataCore team was very valuable in terms of saving us time and money. Throughout the entire process they provided candid, insightful assessments and market intelligence that brought real value to Vix.”
-

Dan Wilson
Principal Architect III @ Concur“The StrataCore team is exceptionally talented, knows the industry, and always delivers on promises.”
-

Carey Fujii
Former IT Director @ Tableau“What I enjoy most about StrataCore is their full end-to-end service. We met, gave StrataCore our requirements, and they engaged the appropriate vendors.”
-

Clifford Cancelosi
COO @ MultiScale Health Networks“StrataCore focuses on completely understanding customer needs/timeframes/etc.They ensure that it's accurately represented to the provider community.”
-

Jason Stefanski
Chief Information Officer & Principal @ GeoEngineers“StrataCore saved us countless hours. Their knowledge of the market and negotiation tactics resulted in saving us a substantial amount. We would not hesitate to recommend them as a very trusted advisor!”
-

Benny Zaidenberg
Sr. Director, Global Data Center & IT Ops @ Amdocs“Working with StrataCore was easy. It’s the best deal and a win/win situation for both our companies.”

