
Venom, announced recently by security intelligence firm CrowdStrike, is a vulnerability affecting the floppy drive emulation code used by many virtualization platforms. It looks like Venom will not be as big as Heartbleed, the vulnerability discovered last year that allowed hackers to grab data from the memory of servers running affected versions of the open-source OpenSSL encryption software. However, VENOM is of particular interest to cloud-users everywhere as it is one of a very few vulnerabilities at the hypervisor that compromises the security through isolation promise of virtualization-based cloud infrastructure.
VENOM, “Virtualized Environment Neglected Operations Manipulation”, is found in open-source computer emulator QEMU, and dates back to 2004. Many modern virtualization platforms, including Xen, KVM, and Oracle’s VirtualBox, include the buggy code. VMware, Microsoft Hyper-V, and Bochs hypervisors are not affected by this bug. The cause is a legacy virtual floppy disk controller that, if sent specially crafted code, can crash the entire hypervisor and allow a hacker to break out of their own virtual machine and access other machines.
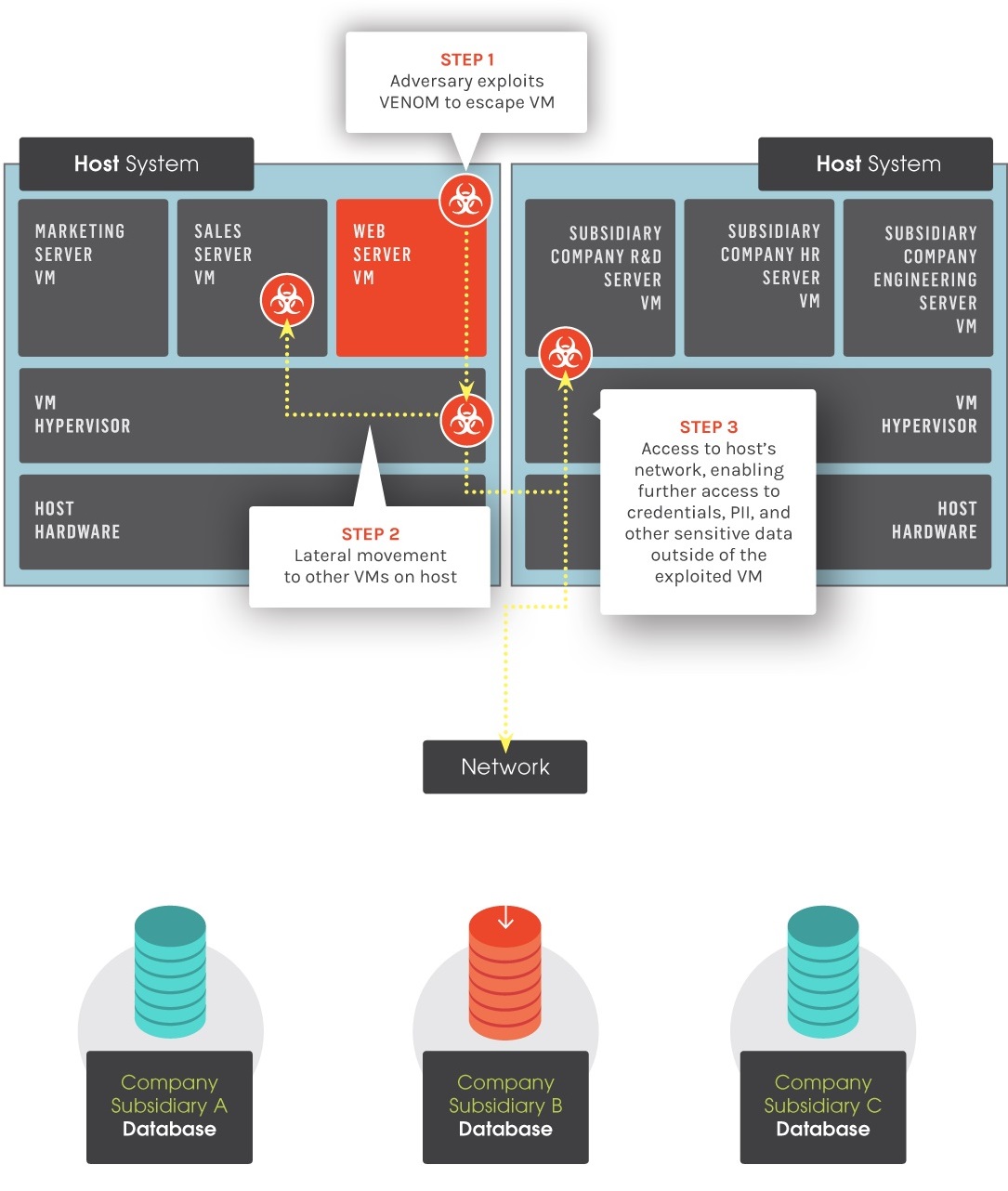
image credit – CrowdStrike
Businesses running applications on virtual machines or running multiple operating systems on one single server in a data center may be at risk. The virtualized systems being used are designed to share resources but remain as separate entities in the host hypervisor, which powers the virtual machines. A hacker can exploit this newly-discovered bug to gain access to the entire hypervisor, as well as every network-connected device in that data center.
If your VM deployment is vulnerable, unpatched, and the administrator account is compromised – or the administrator is malicious – Venom is a real threat. In this case, patches to fix this problem have been released and should be installed as soon as possible. Otherwise, it’s something to be aware of, and talk about around the water cooler for the next few days.
Open source giant Red Hat issued an advisory guiding users to the proper fixes, noting its OpenStack and Enterprise offerings were affected. Citrix said it was looking into the issue, which most likely indicates other OpenStack partners are affected. Rackspace sources said the issue does affect some of its cloud servers. “We have applied the appropriate patch to our infrastructure and are working with customers to fully remediate this vulnerability”. For all you AWS folks out there, here is an update from AWS, stating that there is no risk to their customers.
While it appears that most cloud service providers have addressed the vulnerability, and we will not be seeing the mass cloud reboots of the recent Xen bug, it certainly highlights the need to be a careful cloud consumer. Always get confirmation from your provider that the latest global-scale vulnerabilities have been designated as non-issues or successfully remediated.




